INTELLIGENCE VALUE
The ReSCIND program leverages well-established cognitive vulnerabilities and human limitations to impede cyber attackers. ReSCIND solutions will expand the traditional cyber defense toolkit to help cyber defenders protect National Security Systems and other intelligence community (IC) assets across various phases of a cyber attack.
SUMMARY
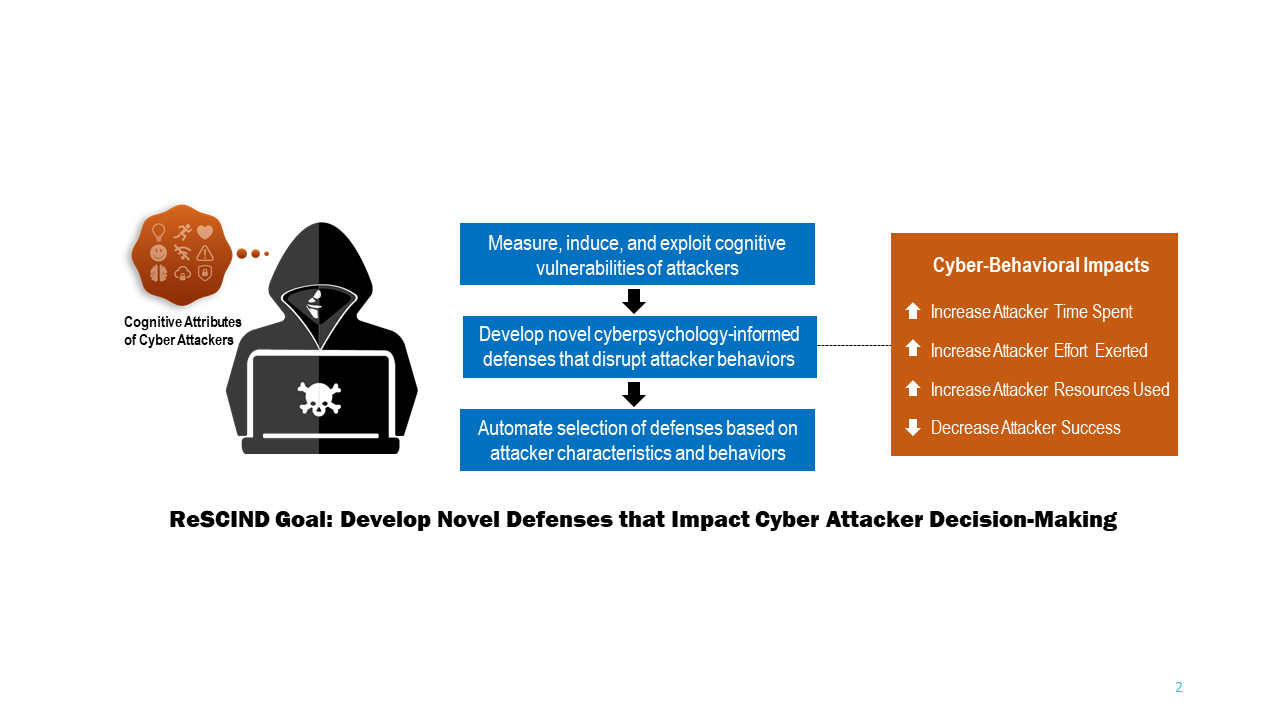
The ReSCIND program develops novel methods to make cyber attackers less effective by impacting cyber attacker decision-making. Traditional cyber defenses typically focus on detecting and stopping suspicious movement on the network; by contrast, ReSCIND performers will develop solutions that exploit attacker cognitive vulnerabilities and limitations to increase the time, effort, and resources spent by cyber attackers. To support and protect the IC mission, the ReSCIND program’s objectives are to: 1) identify cognitive vulnerabilities or limitations relevant to cyber attack behavior, 2) develop technology to induce and measure cognitive vulnerabilities in the cyber domain, 3) measure the impacts of novel interventions on cyber-attacker decision-making and behavior, 4) provide algorithms for automated adaptation of the solutions, and 5) develop cyber-specific computational cognitive models based on observed cyber operations behavior.
Performer solutions will take advantage of psychological vulnerabilities, such as innate decision-making patterns and human limitations, to impact an attacker’s judgment and decision-making. Performers will create cognitive vulnerability sensors to measure the presence of a cognitive vulnerability using typically available cyber data, as well as cyber triggers that activate or enhance cognitive vulnerabilities. Performers will combine sensors and triggers to create cyberpsychology-informed defenses (CyphiDs). ReSCIND aims to develop cyberpsychology solutions that delay or thwart attacks by causing impacts to cyber attacker decision-making that diminish attacker success and result in wasted attacker time, effort, and resources.
Performer solutions are submitted to the ReSCIND Testing & Evaluation (T&E) teams for controlled experimentation through human subjects research (HSR) with cyber experts. The ReSCIND program began in 2023 and has a duration of 45 months. The program comprises three phases, including an 18-month long phase one, a 15-month long phase two, and a 12-month long phase three.
ReSCIND Data Sets
The 20+ HSR studies performed as part of the ReSCIND program have amassed a wealth of data, including cyber and human psychometric, decision-making, and behavioral data, under differing conditions and among different populations, measuring human cognitive vulnerabilities in relation to cyber behavior.